- Nikto Scan Cheat Sheet
- Nikto Cheat Sheet Sans
- Nikto Cheat Sheet Printable
- Nikto Cheat Sheet Download
- Nikto Cheat Sheet Excel
- Nikto Cheat Sheet 2019
What is the Nikto
Nikto is a free software command-line vulnerability scanner that scans web servers for dangerous files/CGIs, outdated server software and other problems. It performs generic and server type specific checks. It also captures and prints any cookies received. The Nikto code itself is free software, but the data files it uses to drive the program are not.
Features
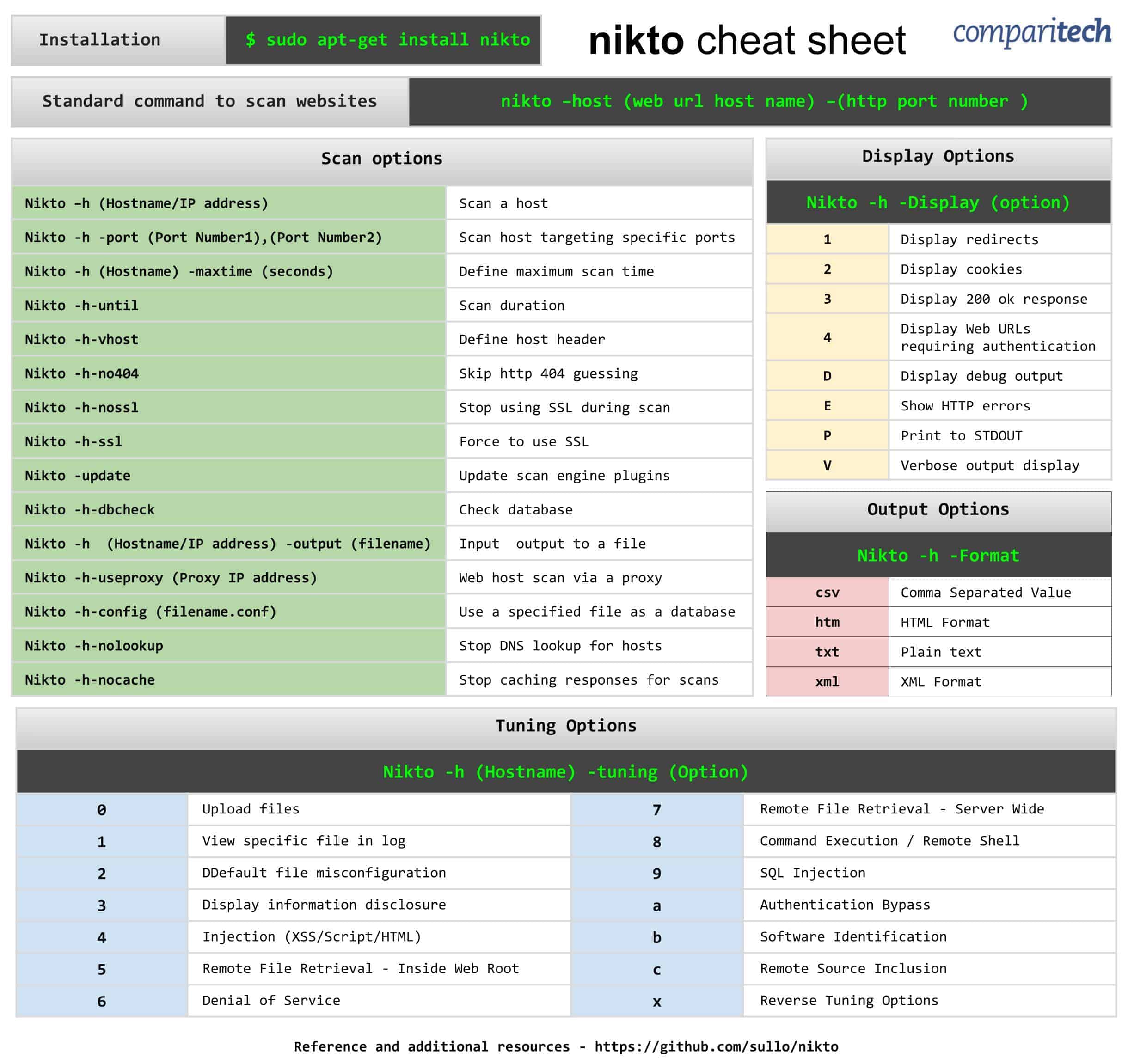
Installation $ sudo apt-get install nikto nikto cheat sheet Standard command to scan websites nikto –host (web url host name) –(http port number ) Scan options Nikto –h (Hostname/IP address) Scan a host Nikto -h -port (Port Number1),(Port Number2) Scan host targeting specific ports Nikto -h (Hostname) -maxtime (seconds) Define maximum.
- Nikto Cheat Sheet Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers.
- JustTryHarder, a cheat sheet which will aid you through the PWK course & the OSCP Exam. (Inspired by PayloadAllTheThings) Feel free to submit a Pull Request & leave a star to share some love if this helped you.
- To scan for vulnerabilities use Nikto. $ nikto -h WebServer is Open. If Port 80 or 443 is open, we can look for robots.txt to check for hidden flags or clues. To find the Webserver version, Use Curl tool with I flag.
Nikto can detect over 6700 potentially dangerous files/CGIs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files and HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
How to install Nikto in Kali Linux
Now, let’s see how to install this tool in our Kali Linux operating system. In this case I have already installed this tool. But I’m show you to how to do this.
In my case it show nikto is already installed.
Now let’s move on.
Nikto Cheat sheet
All of these attacks are against the Metasploitable 2 vulnerable operating system.
Nikto Scan Cheat Sheet
Scanning a host
Scanning specific ports on web server
Nikto Cheat Sheet Sans
Maximum scan time
Scanning duration
Disable SSL
Force SSL
Disable 404 guessing
Ignore negative responses. 302,301
Update the plugins and databases
Specify host header
Output results
Scanning through a proxy
Host authentication
Database check
Config file
Disable name lookups on IP addresses
Disable response cache
Disable interactive features
Display options
1 Show redirects
2 Show Cookies
3 Show 200/OK responses
4 Show URL requiring authentication
D Show debug output
E HTTP Errors
P Print progress to STDOUT
S Scrub output of IP and Hostname
V Verbose output
Evasion Options
1 Random URI Encoding
2 Directory Self-Reference /./
3 Premature URL ending
4 Prepend long random string
5 Fake parameter
6 TAB as request spacer
7 Change the case of the URL
8 Used windows directory separator
A Use a carriage return (0x0d) as a request spacer
B Use binary value (0x0b) as a request spacer

Output File Format
csv Comma-separated-value
htm HTML Format
msf+ Log to Metaspoloit
nbe Nessus NBE
txt Plain text
xml XML Format
Tuning
Nikto Cheat Sheet Printable
1 Interesting file
2 Misconfiguration
3 Information Disclosure
4 Injection (XSS/Script/HTML)
5 Remote File Retrieval – Inside Web Root
6 Denial of Service
7 Remote File Retrieval – Server Wide
8 Command Execution – Remote Shell
9 SQL Injection
0 File Upload
a Authentication Bypass
b Software Identification
c Remote Source Inclusion
x Reverse Tuning Option
Nikto Cheat Sheet Download
Mutate
Nikto Cheat Sheet Excel
1 Test all files in root directory
2 Guess for password file names
3 Enumerate user names via apache
4 Enumerate user names via cgiwrap
5 Attempt to brute force sub-domain names
6 Attempt to guess directory names from a file.
Nikto Cheat Sheet 2019
In this tutorial, we learned about Nikto, a vulnerability scanner written in the Perl programming language. First, we learned how to install the tool. we ran it against our target and explored some of the various options it ships with.now you know how to use it. Let’s Go!